
Update coming for a process to do a weekly update of the CSV files from MaxMind to use more current files than the included ones in the ADC firmware.
So you have some compliance you need to meet on your IRS1075. You might see one of those points that you have to restrict based on origin country IP. Well… That can be a little bit of fun (note below on how that can be fun). So you will need to logon to your ADC with your super secret squirrel account to change the laws of access. For this, I would recommend using the all powerful command line. There is a link to a CTX article that explains parts of this https://support.citrix.com/article/CTX130701/how-to-use-netscaler-to-block-access-to-a-website-using-a-location-database-based-on-users-country
In this example, I’m using Ubuntu on WSL for that Windows / Linux immersive experience.

Login to ADC with SSH.

This is using the inbuilt csv that is part of the firmware that is in the ADC from firmware 11.0. You can use an external file as well which is outlined in the CTX130701 article.
Enter in “add locationFile “/var/netscaler/inbuilt_db/Citrix_Netscaler_InBuilt_GeoIP_DB.csv””
Hit enter and it will report “Done.”
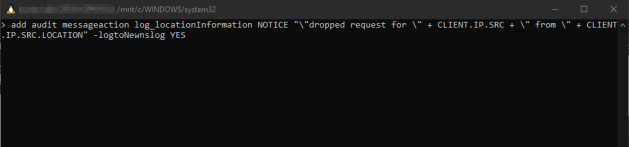
Enter in “add audit messageaction log_locationInformation NOTICE “\”dropped request for \” + CLIENT.IP.SRC + \” from \” + CLIENT.IP.SRC.LOCATION” -logtoNewnslog YES”
This will create the audit log that you can associate to the Responder Policy to write out to whatever syslog you are using.

Enter “add responder policy Drop_non_US_IRS1075 “CLIENT.IP.SRC.MATCHES_LOCATION(\”.US....\”).NOT && CLIENT.IP.SRC.MATCHES_LOCATION(\”.CA....\”).NOT && CLIENT.IP.SRC.IN_SUBNET(10.0.0.0/8).NOT && CLIENT.IP.SRC.IN_SUBNET(172.16.0.0/12).NOT && CLIENT.IP.SRC.IN_SUBNET(192.168.0.0/16).NOT” DROP -logAction log_locationInformation”
This will allow all USA and Canada IPs, and the private addresses for the internal users. If you leave that part off, well…. they aren’t gonna connect internally. This is assuming you want to allow all the private internal IP ranges. You can narrow that further if you wish to be more restrictive. **this is note referenced above**

Enter “set locationParameter -matchWildcardtoany YES” This is for NetScaler 11.1 build 53.11 and above. This is referenced in the CTX article.

Enter “show locationparameter” and it will show the loaded csv file and the “Match wildcard qualifier to any: YES”

You have the audit log configured and the Responder Policy configured. You will need to now bind it to your vservers to apply the policy.
Enter “bind lb vserver <vservername> -policyName Drop_non_US_IRS1075 -priority 100”
I would definitely recommend testing this on an internal testing site so as not to break your production environment. Happy restricting!























